Net Alert
Alert!
UC Browser Leaks Personal Data
Research Summary
UC Browser
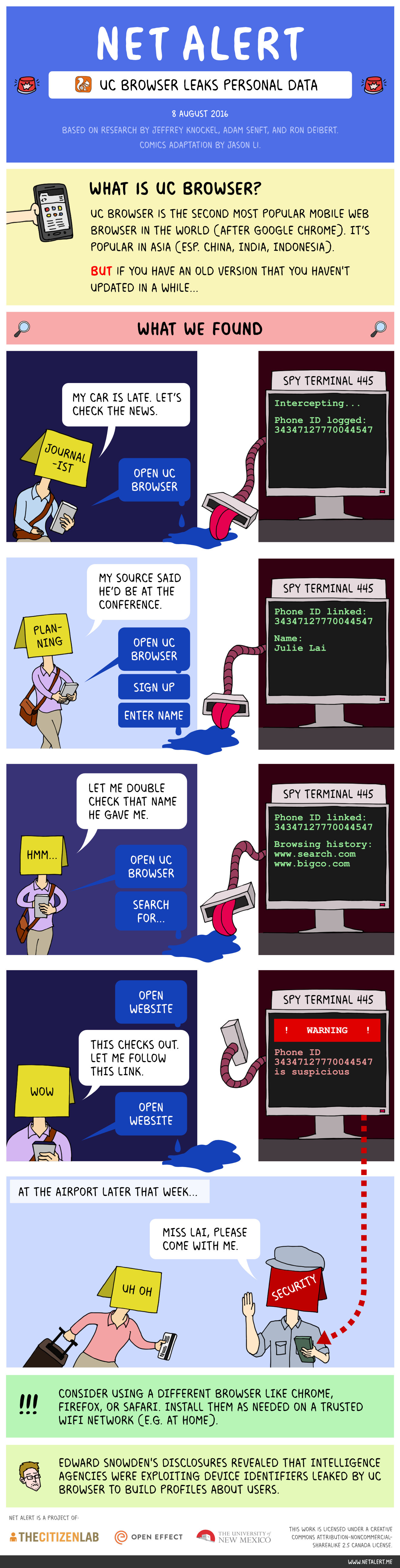
 One of the world’s most popular web browsers did not protect its data transmissions, which can leave personal data at risk of being collected by criminals and intelligence agencies.
One of the world’s most popular web browsers did not protect its data transmissions, which can leave personal data at risk of being collected by criminals and intelligence agencies.
 UC Browser is popular in China, India, and Indonesia. Leaked Snowden documents showed that security problems in UC Browser were being exploited by spy agencies.
UC Browser is popular in China, India, and Indonesia. Leaked Snowden documents showed that security problems in UC Browser were being exploited by spy agencies.
We found two security problems
UC Browser insecurely transmits sensitive personal data
Most apps’ privacy policies claim that they take steps to protect their users’ personal information like your location, browsing history, and information about your devices that can identify you. Protections are particularly needed during transmission of your data from the app to the Internet. When data leaves your phone it passes through many points along the Internet before finally reaching its intended destination. At any of those points, if your data is sent insecurely, our data can be collected by would-be criminals and spies.
UC Browser used weak cryptography, and sometimes no encryption at all, when it transmitted keystrokes as a user entered in website addresses or search terms or when a user’s location was beamed out over the Internet. Many of those transmissions included sensitive device identifiers that make it easy to collect and analyze the traffic particular to a single individual and build up a massive profile of interests and activities over time -- gold for criminals and spies.
An old version of UC Browser had problems with its software updates
When you update software,you download new code that is then applied to the program. Software should make sure this download is trusted by verifying who delivered the code by checking the code’s cryptographic signature. This helps stop would-be hackers from replacing the actual code with dangerous malware.
UC Browser used weak cryptography for part of its software update process, leaving its users vulnerable to malware attacks by criminals and spies who could take control of their devices. This problem has been fixed in newer versions of the browser, but based on documents leaked by Edward Snowden, we suspect the problem may have been used by intelligence agencies to install malware on their targets’ phones.
Concerned users of UC Browser should consider installing a different browser like Chrome, Firefox, or Mobile Safari. Download these browsers directly from their company's website or a trusted app store. Make sure you do this on a trusted network like your home.
Read the full report by Jeffrey Knockel, Adam Senft, and Ron Deibert.



